Cyber security is a very real risk for businesses today, as we rely on technology more and move a lot of our information online. Small businesses are at risk from cyber criminals, who target them because their systems are probably easy to attack.
Unfortunately, many smaller companies don’t invest time or money into protecting their systems and data. When you’re busy and you’re responsible for staff and the day to day business activities, it’s hard to add something else to your priority list.
We’ve put together this seven-step plan so you can protect your information and make sure you don’t end up a victim of a cyber criminal.
Table of Contents
- Cyber Security Statistics for Small Businesses in Connecticut
- What Does Good Cyber Security Look Like?
- How Companies Benefit from a Cyber Security Plan
- A Seven Step Guide to Creating Your Own Cyber Security Plan
Cyber Security Statistics for Small Businesses in Connecticut
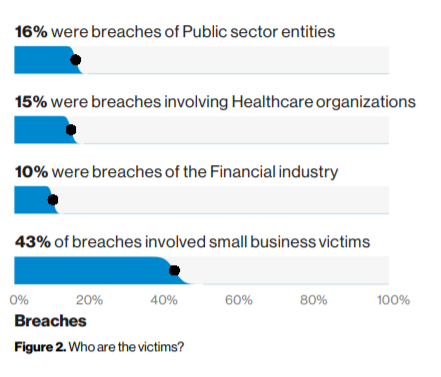
The recently published 2019 Verizon Data Breach Investigations Report (DBIR) helps us understand what the most common security incidents are and who are the most targeted. It states that out of 41,868 security incidents in 2018, 43% involved small business victims. Also, it reveals that even though external actors are still the primary culprits, the internal threat is on the rise.
In Connecticut, a law enacted at the end of 2018 requiring businesses who had suffered a data breach to offer credit monitoring and free identity theft protection to individuals who have had their Social Security details stolen. This shows how serious the threat is for CT based businesses and non-profits.
Furthermore, a CBIA (Connecticut Business & Industry Association) survey in 2018 found that: “almost a quarter of Connecticut businesses suffered data breaches or cyber attacks in the last two years, with 26% unsure of the sources behind those incident.”
What Does Good Cyber Security Look Like?
So, what is cyber security and how do you make sure you get it right? Essentially, cyber security is about protecting all the electronic devices within your company, and the information on it as well.
This includes laptops, tablets, smartphones and any personal devices your employees have which they sometimes use to access work from outside of the office.
A more formal definition of cyber security is: “Prevention of damage to, protection of, and restoration of computers and electronic communication systems." It’s easy to see why this is important for businesses.
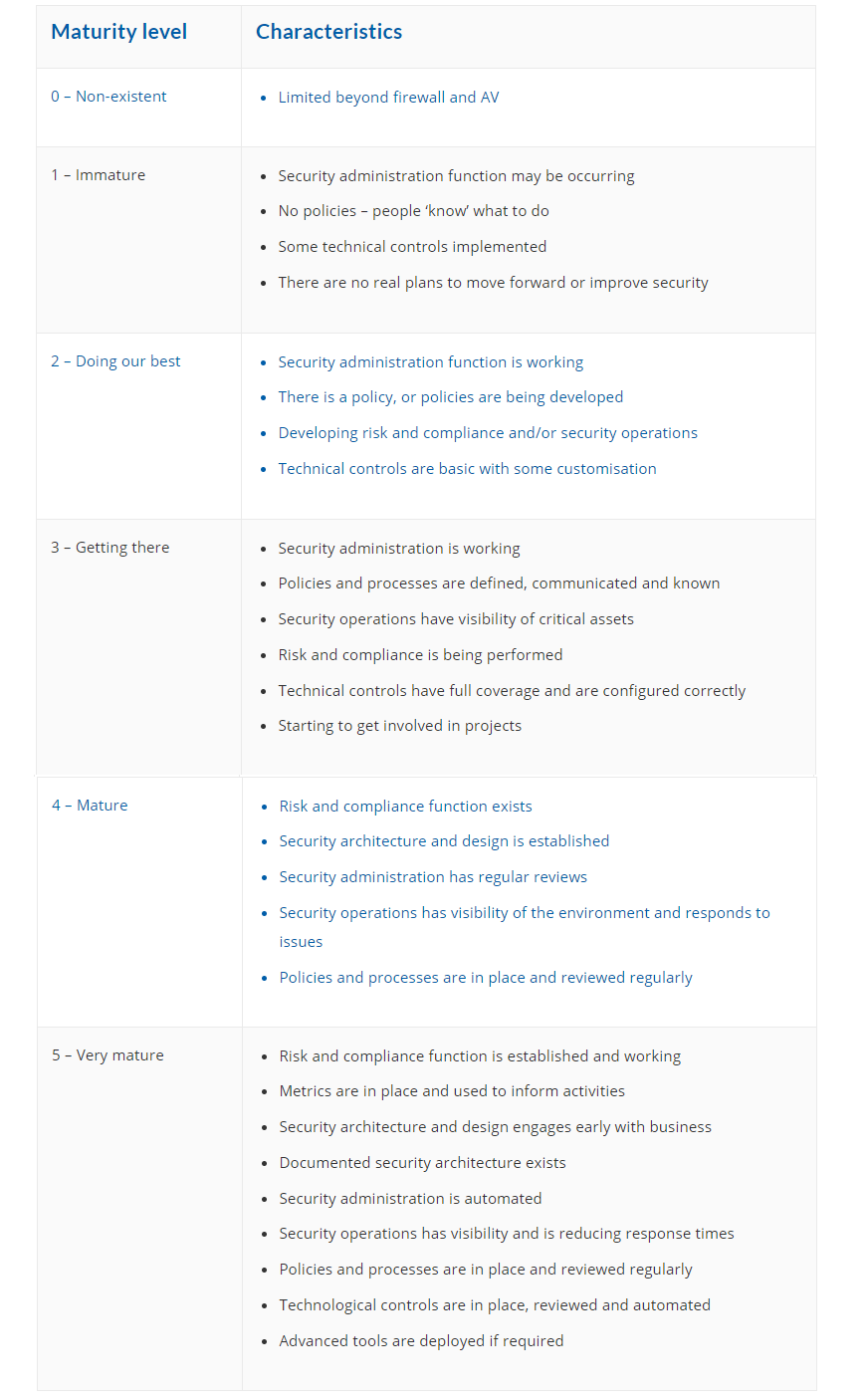
Before you start putting your plan together, it’s worth taking time to assess where you are now. Whether you have an in-house IT department or you outsource support, speak to them to see what procedures they have in place to keep your data safe.
Since this is your first, or one of your first, cyber security plans, your company’s security maturity is most likely at stage 1 or 2 of the chart above. However, don’t worry, this guide will help you create a roadmap that will improve your security posture by a level simply because you’ll know what questions to ask a professional or IT provider.
By spending time on developing your cyber security plan, you’re being proactive. This is much better than a reactive approach that is way more stressful and costly in every respect!
How Companies Benefit from a Cyber Security Plan
All businesses hold some information on their clients, and depending on what it is you do, you may store a lot of sensitive customer data. A proper plan helps you to protect that information, and also reassures your clients that you’re committed to ensuring their privacy.
A system breach can have long-reaching ramifications. If you don’t have a process in place that can reduce the chance of a hack or restore data quickly if the worst happens, your business is seriously compromised.
You risk losing clients, trust and income, and you won’t be able to operate properly until things are fixed. Depending on how long this goes on, or if you have multiple breaches, there’s a very real likelihood of your business actually going bust.
Having a cyber security plan in place demonstrates your understanding of the potential threats and that you’re focused on reducing and eliminating these, which makes you more attractive to potential customers.
Also, having a plan in place can also be a requirement when bidding for IT consulting projects, particularly with government or military organizations. Make sure you don’t miss out on opportunities to win clients and grow your business.
A Seven Step Guide to Creating Your Own Cyber Security Plan
Now you understand the importance of having a cyber security plan and what makes a good one, we’ll take you through the process step by step. Follow these, and you’ll have a solid strategy in place to secure your small business’ data.
Step 1 – Identifying and Understanding Security Risks
The most important thing to do is to identify and understand your risk, so you know what it is you want to protect. You probably don’t want or need to protect everything, so work out your business priorities.
It’s helpful to understand that you can’t eliminate all risk, and it's unreasonable to think you can protect every piece of information in the business. But, you do want to understand where you have the most risk and what it is that you can protect.
An easy way to get started is to make a list of everything within your business that you think is worth protecting. Note down everything that comes into your head, and cross anything off the list that isn’t important when you review it later.
At this point, don’t be too specific or think about it too much – just get things down. You can do this with paper and pen, in a Word document or a spreadsheet. You might want to create a shareable document for senior staff to add in their priorities too.
Things you might include are your hardware, software and applications. Note down the make, model and serial number of all equipment you have, including mobile devices. Also include things that are outside of your business but are essential, such as cloud applications and devices.

Then, identify your threats and vulnerabilities. To help you with this, you could hire an external company to carry out a vulnerability test to find where you’re most vulnerable so you know where to start with protecting your systems.
A vulnerability scan will help you understand your risk profile based on the industry you’re in and the size of your company.
A key point to remember about vulnerability scans is that every new device you buy should be scanned before use, and again after any update. Scans should be carried out at least quarterly.
A scan will also identify any unauthorized changes on your system, and identify the cause, whether that’s staff error or a malicious attack.
Take the information and get started immediately. Make sure you limit employee access to data and information while you’re implementing your plan.
Step 2 – Protecting Data from Internal and External Threats
One mistake many companies make is to give their employees access to almost all the information they have, or don’t realize that all staff have the same permissions. Make sure that you review everyone’s access and limit it to only the specific information they need to do their jobs.
Have a policy in place that when an employee leaves the company you remove their access to your data, so they can’t use or compromise it for their own benefit. Include remote access as well.
Next, you might want to think about a UPS (uninterruptible power supply) and surge protectors. A UPS will help if the power goes out, so consider putting one on the machine which holds all the information, and on your server if you have one.
A surge protector safeguards your electronic devices against voltage spikes which could cause damage. Know how much battery you need to keep things running, and check these regularly.
Hackers look for weak spots in operating systems, so if you’re not using an outside IT partner, you need to be aware of the latest patches and updates from your operating system provider (e.g. Microsoft) and make sure these are applied.
We mentioned earlier that a firewall is an important thing for all organizations. Don’t just install it and forget about it – monitor, manage and update it. Be aware that your firewall will need replacing sooner than your PCs and server.
Secure and segment your wireless, so if customers and vendors have access to it, they are given a separate login and ideally, their own network too. Remind your staff not to access unknown networks on their mobile devices while away from the office.
For remote workers, you might consider a VPN or virtual provide network, to add an extra layer of security. Include email filters to reduce the risk of phishing and malware, and set up encryption, particularly if you send and receive sensitive information. Encryption today is straightforward.
When you dispose of out of date equipment, make sure you destroy or electronically clear the hard drive. You can hire a company to do this for you and they’ll issue you with a certificate of acknowledgment to confirm the data is destroyed.
Step 3 – Detecting Malware
Looking for malware is vital. Install an antivirus program and spyware, and make sure these are maintained and monitored. For small businesses, this is so important that it might be worth investing some of your cyber security budget with an outside company to do this for you.
It’s not enough just to have antivirus installed, unfortunately, you need to analyze the information the tool is giving you. Remember that the software is designed to find malware on your devices, remove it and fix any damage it might have caused.
Some AV programs can even run continuously in the background to prevent malware installing itself, as well as real-time protection and website blocking to keep you safe from sites which could infect your devices.
Step 4 – Installing and Updating Software Regularly
Part of your business review should include all the software and applications your company uses. If you purchase new software, have this installed by the vendor or your IT team. Don’t allow staff to do this themselves.
Likewise, updates and patches for your operating system should be carried out only by certain people, not by the individual who receives an update notification. Once a software vulnerability has been found by a cyber-criminal, they are able to exploit this for the lifetime of the version. Installing critical and security updates as they become available is key to protecting yourself.
Exercise caution whenever you’re required to visit an external site to download software updates, and be particularly careful of free programs. Again, it may be worth having a policy in place that says your company doesn’t use free software. Avoid download managers and installers, and choose ‘custom installation’ without any additional software.
There is a risk too from download ads that pop up on browsers that take anyone who clicks to a site which then installs malware. Ad blockers and filters should prevent these from appearing on users’ screens. All software should be scanned for malware before it’s downloaded.
Step 5 - Cyber Security Awareness Training for All Employees
Every employee who has access to your online information needs to be aware of the seriousness of cyber crime threats.
Add security awareness training as part of new employee orientation, and take the opportunity to reinforce the importance of passwords, being careful with attachments and links..
You may ask a third-party to deliver this for you,. And make a point of arranging for staff to have additional training and refreshers every quarter or so and, if possible, test employees’ knowledge by including phishing simulators!
Step 6 – Creating a Recovery Plan
Put together a recovery plan that outlines the key roles and responsibilities in the event of a data breach or other security compromise. Identify the decision maker and who initiates the recovery procedure (these are probably the same person).
Do you need to contact your external IT partner? Make sure their details are included in the plan. Next, think about the process your staff need to follow, and document it so that everyone knows what to do if there is an incident.
Include things such as how devices and applications should be shut down, how to contact people if the email server goes down, if any equipment needs to be moved elsewhere, and when the data backup will start. Also factor in how to ensure business as usual until the problem is resolved.
Disaster recovery is a key part of your plan, so ensure that you have a full backup of all of your data so you can restore information as soon as possible. The backup needs to be encrypted, and ideally offsite.
It’s best to have full backups rather than relying on incremental backups, to prevent the loss of critical data. If you only back up once a week, any data that’s changed and then lost after that scheduled backup cannot be restored. Consider daily or even hourly backups instead to prevent major loss. And regularly test your backups so you know they work and you can restore both files and servers.
Produce a comprehensive plan on what your processes are, and put time aside to review and update it as needed. Make it part of staff training, and give employees refreshers on the procedures. In the event of a disaster, you may need to amend your plan to prevent it happening again.
Step 7 – Implementing a Mobile Security Policy
Remind staff not to bring their own devices into the office (or, if you do allow BYOD, have these tested and secured and have their protection updated regularly) and make sure that they don’t download or upload personal data via their work electronics.
Ask them to be careful with installing updates – you may want to implement a policy where these are only done by the IT team, your external provider or a key employee. You don’t want malware installing itself because someone clicked on a fake update notification.
As we said earlier, secure passwords are important, so make sure these are set up on devices and on any programs employees use. Remind staff not to give these out to anyone who asks, or reveal any personal information about themselves or clients if they receive a call or email from someone they don’t know.
Having a cyber security plan means you can keep your information safe and secure, and both limit it being viewed by those outside the organization and prevent it from being used or compromised.